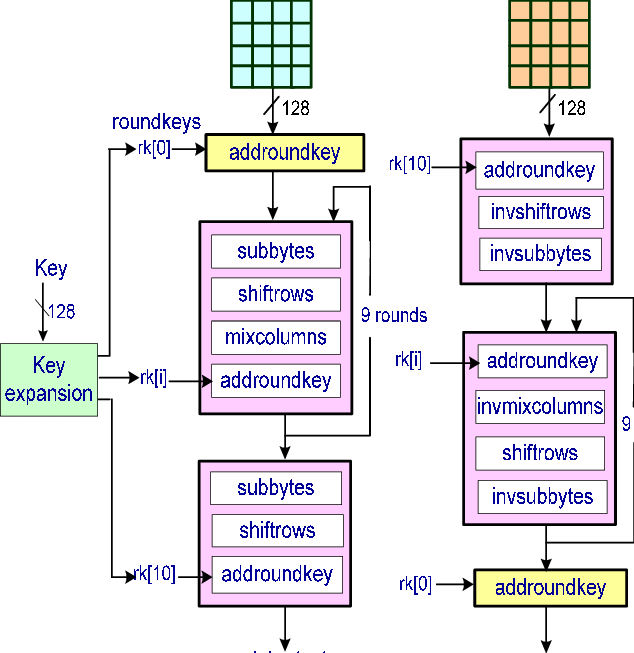
AES algorithm
AES (Advanced Encryption Standard) algorithm was developed by Vincent Rijmen and Joan Daemen in 1998. This algorithm was first known under the name Rijndael and finally it was chosen as the official standard of security communication. This algorithm was first used in various security systems such as Wi-Fi Protected Access (WPA) and VPN.
AES (Advanced Encryption Standard) is one of the most popular and secure symmetric encryption algorithms. This algorithm was chosen by NIST (National Institute of Standards and Technology) as the encryption standard.
How AES works:
Key length: AES can use keys of 128-bit, 192-bit, and 256-bit lengths. Longer key length means more security.
128-bit blocks: The message is divided into 128-bit blocks. Each block is encrypted individually.
Encryption cycles (rounds): the number of encryption cycles depending on the length of the key:
For 128-bit key: 10 cycles
For 192-bit key: 12 cycles
For 256-bit key: 14 cycles
Encryption process:
SubBytes: Each byte is replaced using a fixed lookup table.
ShiftRows: The rows of the matrix are shifted periodically.
MixColumns: Matrix columns are mixed together.
AddRoundKey: Adds a subkey derived from the primary key.
These steps are repeated several times to increase the security of the message.
Advantages:
Speed and efficiency: AES is suitable for both hardware and software due to its efficient structure.
High security: Large key lengths and complex encryption process make AES highly resistant to attacks.
AES (Advanced Encryption Standard) is used in various fields. Some of its practical applications are:
Web browsers: for security of communication between browser and servers.
Unsupervised payment systems: for financial information security.
Covert communication systems: for confidential and secure communication.
Content delivery systems: for digital content security.
Government Information Systems: To maintain the security of sensitive information.
The AES algorithm is known as one of the most secure cryptographic algorithms, and no major hacks that directly break this algorithm have been reported so far. However, side-channel attacks and implementation weaknesses can compromise the security of systems that use AES. For example, timing attacks and power analysis attacks can extract information from AES-encrypted systems.
A practical example of side attack related to AES is Timing Attack. In this type of attack, the attacker obtains information by observing the different times that the system takes to perform different cryptographic operations. For example, if an attacker can observe the different times the system takes to encrypt different blocks, he may have the ability to identify weaknesses in the system's configuration.
A real-life example of this attack was an attack carried out in 2019 by a group of scientists known as a timing attack. . In this attack, by observing the different times the system takes to perform different encryption operations, the attacker was able to obtain information that helped him identify the encryption key.
Timing Attack
In this type of attack, by measuring the times that a system takes to perform cryptographic operations, the attacker can deduce information that is sufficient to break the cryptographic system.
Steps of a timing attack:
Observing encryption times: The attacker repeatedly sends requests to the system and measures the response times.
Difference Analysis: By analyzing the time differences for different requests, an attacker may be able to deduce parts of the encryption key.
Creating a temporal model: The attacker uses the collected temporal data to create a model of how the system processes cryptographic operations.
Key derivation: By using the temporal model, the attacker can deduce parts of the key or the entire key.
Countering timing attacks
To deal with this type of attack, it is recommended to:
Time-constant implementations: Implement algorithms in such a way that their execution time is constant for all inputs.
Adding noise: Adding noise to response times can make it more difficult for an attacker to analyze the times.
More rigorous security testing: Implementations must undergo rigorous security testing to identify and fix vulnerabilities.
We will talk more about encryption algorithms in the future.
